What Is SIEM Software?
Before we start with our SIEM software comparison, it’s important to know what Siem Software is and how it works. SIEM (Security Information and Event Management) software is used to help IT professionals and businesses measure the activity within their environment.
SIEM technology has been around for more than 10 years. It combines both security information management (analyzation, reporting, and collection of log data) and security event management (analyzes real-time data to provide an efficient threat response).
How Is It Used?
SIEM software works by aggregating and collecting log data that’s created through an organization’s technology infrastructure. This ranges from the security devices like antivirus filters and firewalls to host systems.
The software categorizes and identifies events and incidents. Then it analyzes them in order to create the right method to prevent future issues from occurring. SIEM software fulfills these two main objectives:
- Sends alerts if unsuspected activity happens that is against the predetermined rules set by the network. It will view the threat as a security issue and attempt to remove it.
- Gives detailed reports on security events such as malware activity, failed and successful logins, and additional malicious activities presented on the network.
Enterprises that are in need of effective security management need to be early adopters of this technology. Fortunately, we’ll help you by comparing the two top SIEM software available so that you can make the right choice for your business.
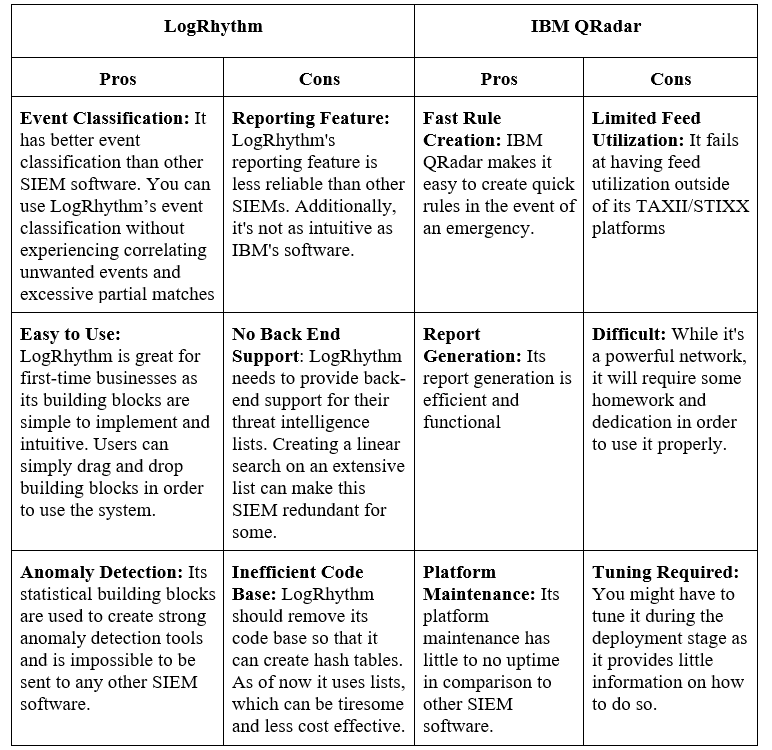
LogRhythm vs. IBM QRadar
This table below demonstrates the key differences between LogRhythm and IBM.
Conclusion
For your money, IBM QRadar is the winner. Not only does it provide greater protection, but also the software assists you in creating a strong network that’s always alert for outside attacks. Thus, get IBM QRadar if you want a reliable SIEM software that will protect your company in the long run.
Sources:
- https://www.csoonline.com/article/2124604/network-security/what-is-siem-software-how-it-works-and-how-to-choose-the-right-tool.html
- http://searchsecurity.techtarget.com/feature/Comparing-the-best-SIEM-systems-on-the-market
- http://www.tomsitpro.com/articles/siem-solutions-guide,2-864-2.html
- https://www.solarwinds.com/siem-security-information-event-management-software
- https://www.alienvault.com/solutions/siem-log-management
- https://www.gartner.com/reviews/customer-choice-awards/security-information-event-management
- http://searchsecurity.techtarget.com/definition/security-information-and-event-management-SIEM
Find a Home-Based Business to Start-Up >>> Hundreds of Business Listings.