Moving your data to the cloud can be liberating! It can unlock tremendous business tools and capabilities to your end users and promote collaboration and team work by removing technical obstacles. Despite the benefits and the robust nature of today’s cloud environments like Office 365, you still need to protect your business data.
Why does Office 365 need protection? Why can data loss happen in Office 365? What best practices can you follow to ensure your data is protected? Let’s cover these topics and see how you can effectively use Office 365 and protect your data at the same time.
Why Does Office 365 Need Protection?
While cloud environments like Office 365 provide tremendously powerful features, data that is totally immune to data loss is not one of them. A point of confusion that leads to misplaced confidence in data stored in the cloud is that cloud resiliency and redundancy means your data “can never be lost”. This is simply not the case.
It is certainly true that the major cloud vendors like Amazon, Google, and Microsoft have resiliency and redundancy mechanisms in cloud infrastructure that most will find nearly impossible to duplicate in their own on-premises data centers. However, even when a system is redundant or resilient, data can still be lost as we will see.
When thinking about the part cloud will play in carrying out your daily business operations, cloud has become a business-critical infrastructure component. If cloud resources are lost, it can be an event that severely impacts business continuity.
The trend in cloud Investment by businesses across the board emphasizes the use of the cloud in business-critical infrastructure in a large way. The below data from Gartner shows the revenue forecast for cloud infrastructure and services. Notably Cloud Management Services (Saas) is the largest area of spending in cloud technologies. Cloud SaaS includes Office 365 and other solutions.
Worldwide Public Cloud Service Revenue Forecast (Billions of U.S. Dollars)
| 2018 | 2019 | 2020 | 2021 | 2022 | |
| Cloud Business Process Services (BPaaS) | 41.7 | 43.7 | 46.9 | 50.2 | 53.8 |
| Cloud Application Infrastructure Services (PaaS) | 26.4 | 32.2 | 39.7 | 48.3 | 58 |
| Cloud Application Services (SaaS) | 85.7 | 99.5 | 116 | 133 | 151.1 |
| Cloud Management and Security Services | 10.5 | 12 | 13.8 | 15.7 | 17.6 |
| Cloud System Infrastructure Services (IaaS) | 32.4 | 40.3 | 50 | 61.3 | 74.1 |
| Total Market | 196.7 | 227.8 | 266.4 | 308.5 | 354.6 |
When you think about the major part that your cloud environment, including Office 365, will play in carrying out your business operations effectively in years to come, it will be absolutely essential that you protect your data that is housed there.
Why Can Data Loss Happen in Office 365?
Why can data loss in Office 365 happen? Data can be deleted or corrupted by either legitimate or malicious actions in Office 365. This can happen even if there is no underlying hardware or system fault in cloud infrastructure. In other words, the resiliency and redundancy of cloud infrastructure may be unaffected and still intact, but data may be deleted. It can simply be due to the actions of a user or potentially, an attacker.
There are two main threats to your data that exists in the Office 365 cloud:
- Ransomware
- End user actions
Ransomware
Ransomware is arguably one of the most ominous threats to your data. Even in cloud environments, ransomware like a plague, can get its tentacles into your data and start slyly encrypting it. Generally speaking, when you notice the encryption of your data, it is too late.
Public cloud vendors are beginning to put protections in place to help fight ransomware and the effects on your data, however, these protections are not perfect. How does ransomware enter your Office 365 environment? File synchronization and Email.
With file synchronization, on-premises Office 365 files are synchronized up to the Office 365 OneDrive for Business cloud. Often, OneDrive storage is shared between departments or different teams of end users. As an example of how ransomware can infect the cloud via synchronization, if one user’s laptop is infected with ransomware, the local OneDrive file copies are encrypted and synchronized up to the OneDrive for Business cloud. This leads to all users connected to this cloud storage location seeing only the encrypted versions of the files stored in the OneDrive cloud.
Email is another attack vector. With Office 365 email, attackers have demonstrated they can encrypt Office 365 user inboxes. An unsuspecting end user simply has to grant permissions to a seemingly legitimate program that launches a ransomware attack on their inbox. Within minutes, their entire inbox will be encrypted.
End User Actions
Another way data loss can happen in Office 365 is due to end user actions. Users carrying out a file operation they assume to be safe find they have deleted the wrong file or folder or have updated the wrong file. They may even perform a bulk delete operation on the wrong data.
Again, Office 365 infrastructure may be operating normally, however, your data is affected by end user actions that can result in data loss. Resiliency and redundancy of the cloud infrastructure will not protect your data in these cases.
Office 365 Protection Best Practices
With the importance of protecting your cloud data well-established, following best practices when it comes to protecting your Office 365 environment helps to ensure reasonable measures to both protect and secure your Office 365 cloud data.
Let’s take a look at a list of the things you should be doing to provide reasonable protection to your Office 365 environment. This includes:
- Enforce Strong User Passwords
- Enable Banned Passwords
- Enable Multi-Factor Authentication (MFA)
- Configure and Enable Risk Policies
- Use the Security and Compliance Center Secure Score
- Use Role-based Access Control (RBAC)
- Encrypt Email Messages and Use Blocking Rules
- Configure Mobile Device Management (MDM)
- Allow OneDrive Syncing Only from Specific Devices
- Backup Your Office 365 Environment
1. Enforce Strong User Passwords
Passwords are one of the most basic aspects of securing today’s business-critical systems both on-premises and in the cloud. Making sure the passwords used by end users are strong passwords comprised of mixed-case, special characters, and numbers is one of the most basic ways to improve overall Office 365 security. Enforcing strong passwords helps to protect your Office 365 environment from data loss due to compromised accounts.
End users have a tendency to use easy-to-remember, non-complex passwords. These types of passwords are easy for attackers to brute force and compromise with “dictionary style” attacks. Using Azure AD which is provided with Office 365, you can enforce strong passwords globally. This requires all Office 365 users to make use of strong passwords when setting their Office 365 password on their account.
IT Admins can check to see if strong passwords are required in their Office 365 environments by using the following Azure AD PowerShell cmdlet:
- Get-MsolUser | ft -auto UserPrincipalName,StrongPasswordRequired
2. Enable Banned Passwords
Even when enforcing the use of strong passwords, there are patterns or words that can comprise a password that may still be easy to guess. Microsoft constantly examines telemetry data from Azure and looks for common patterns and potentially compromised passwords.
The Azure AD service has a means to turn on banned passwords using a default list from Microsoft that includes compromised passwords discovered in their telemetry data. You can also set custom banned passwords. Using banned passwords can greatly help to protect your Office 365 environment from data loss as a result of security breach.
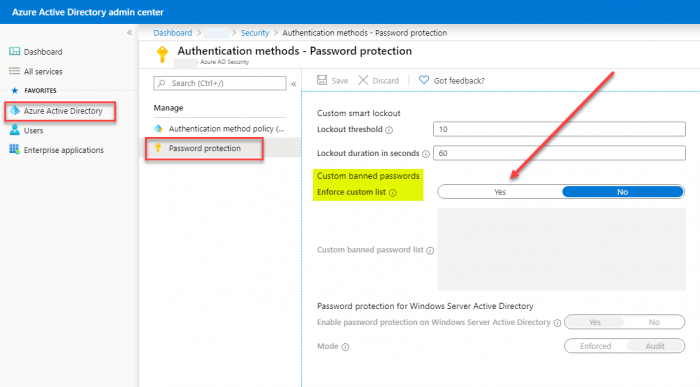
3. Use Multi-Factor Authentication
Even with the above mechanisms in place to help secure end user passwords, passwords alone are no longer sufficient in themselves to ensure the security of your Office 365 environment. Due to sophisticated and very convincing phishing attacks and social engineering, end users can be tricked into sharing usernames and passwords with an attacker.
Multi-Factor Authentication helps to protect your Office 365 environment by providing an additional layer of security with a second form of authentication. This includes using a mobile device such as a phone as part of the authentication process.
Even if the correct password is known, a second form of identity validation is needed. If an attacker has possession of the password, they still do not have all they need to complete the identity verification process. This greatly helps to reduce the ability of an attacker being able to compromise an account.
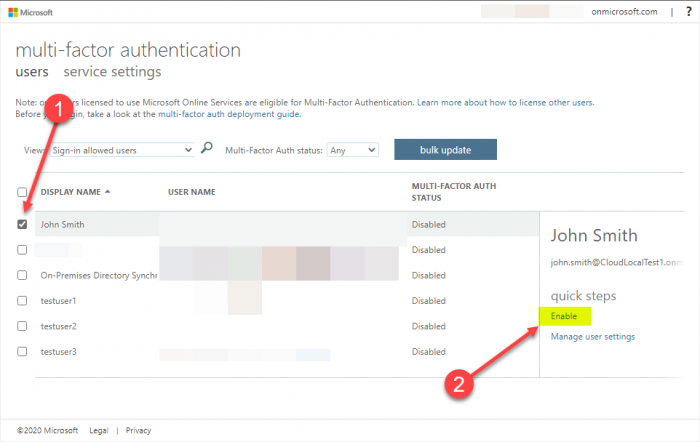
4. Configure and Enable Risk Policies
Used in conjunction with Multi-Factor Authentication, Azure AD Identity Protection can bolster the security of your Office 365 environment by the use of risk policies. There are two kinds of risk policies that help to protect your Office 365 environment:
- Sign-in risk policy
- User risk policy
Using machine-learning, Office 365 can determine if sign-ins to a user account are from a legitimate user or if the attempt is a result of an attack. In addition, user activities can be screened for what look to be malicious or compromised user activity for a particular account.
With both of these risk policies, Office 365 can intelligently decide to block access, allow access, or allow access but require a password change from the end user.
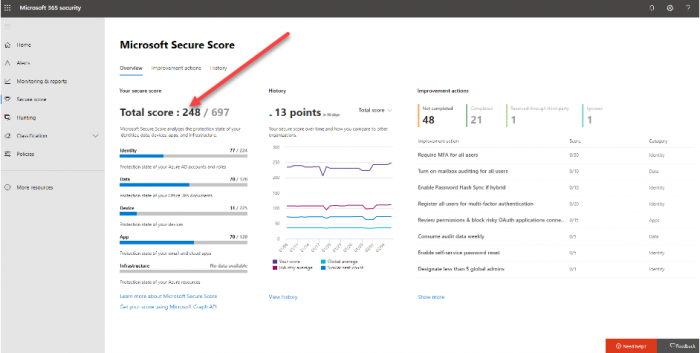
5. Use the Security and Compliance Center Secure Score
Discovering security and compliance hot spots in your Office 365 organization can be a daunting task. However, with both the Security and Compliance Secure Score values, you can quickly understand potential “hotspots” in terms of security and compliance in your Office 365 environment.
The Secure Score in the Security and Compliance Center is a measure of both the security posture and compliance with regulatory standards. This allows having quick visibility to known security or compliance issues in your Office 365 organization. While the Security Center Security Score has been around for a while, the Compliance Score is a new offering that Microsoft released recently in conjunction with Microsoft Ignite 2019.
The Secure Score helps your organization in several key areas:
- Have visibility to your current Office 365 security posture
- Improve your overall security posture via the recommendations given
- Establish key security performance indicators and understand risk factors
6. Use Role-based Access Control (RBAC)
One of the key areas that can be used to ensure security and compliance in your Office 365 environment and by extension, protect your data, is using Role-Based Access Control (RBAC). RBAC establishes a “least-privilege” model where a user is only assigned the required permissions they need to carry out their job role.
All too often, a user may possess more permissions to resources than he or she needs to fulfill their job role. This creates security risk in the environment. If the over-provisioned user account is compromised, an attacker now has all of the extra permissions to data and systems that are above and beyond what the end user needed in the first place.
Using RBAC, access control is granted based on the role a user plays in the Office 365 organization. Using the built-in tools that are provided with Office 365 for establishing user permissions across the various systems, you can ensure that users are only assigned those roles and permissions they absolutely need to carry out their job duties.
7. Encrypt Email Messages and Use Blocking Rules
Email is one of the day-to-day business-critical systems that is used to support business activities. It can store a huge amount of information for your business. Often, much of that information can potentially be sensitive or contain information that you do not want to be openly exposed. Examples can include banking data, health information, or other Personally Identifiable Information of customers.
There are different encryption options available for Office 365 Email. These include:
- Office Message Encryption (OME) – Build on top of Azure Rights management service. Messages can be encrypted using Rights Management templates. Administrators can define mailflow rules to require encryption
- Secure/Multipurpose Internet Mail Extensions (S/MIME) – Office 365 Exchange administrators can enable S/MIME for the organization which sends digitally signed and encrypted messages
- Information Rights Management (IRM) – This is used to prevent information leakage for online and offline protection of email messages
- TLS – Encryption used to secure mailflow on various Exchange connectors to protect sensitive email information
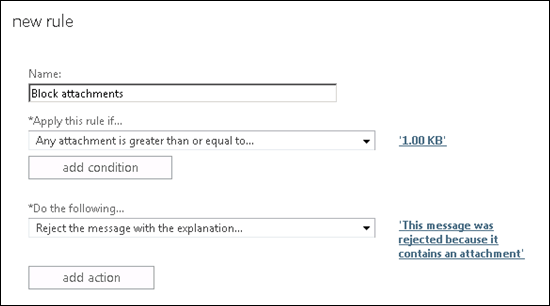
In addition to email encryption, blocking file types and attachments that are absolutely not needed is a great way to help reduce the attack vector for dangerous file types and potential ransomware infection. Making use of Blocking Rules in Exchange Online to block dangerous attachment types can be a great way to help secure and protect your Office 365 data.
8. Configure Mobile Device Management
Mobile devices have become a staple of business productivity, especially with cloud environments like Office 365. However, with the added productivity and mobile connectivity capabilities that come from allowing end users to utilize mobile devices, there are security implications to this as well.
Office 365 provides the ability for Mobile Device Management (MDM). This functionality is built-in with Office 365. It helps you secure and manage end user devices such as Androids, iPhones, iPads, and Windows mobile devices. This allows many great features and functionality from a device management standpoint.
Capabilities like assigning security policies, remotely wiping a device, and reporting features are all possible with the MDM features in Office 365. This bolsters your ability to protect your Office 365 environment from data loss or data leakage.
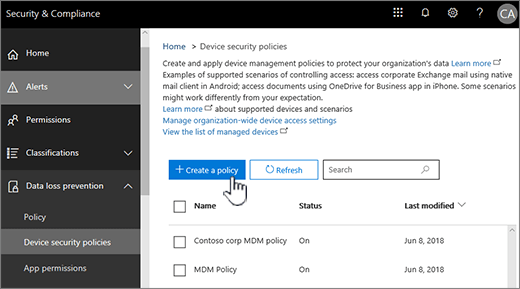
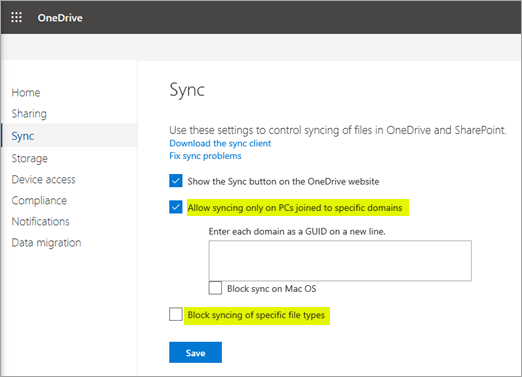
9. Allow OneDrive syncing only from specific devices
As mentioned earlier, file synchronization can lead to the spread of ransomware infected files from on-premises up to your Office 365 cloud environment. While it may not be feasible to eliminate file synchronization across the board for every device, you may want to allow OneDrive syncing only from specific devices or PCs joined to specific domains.
This helps to ensure that users can synchronize OneDrive files only on managed computers controlled by your organization. As you can see below, you can:
- Allow syncing only on PC’s joined to specific domains
- Block syncing of specific file types
10. Backup Your Office 365 Environment
Backing up your data in Office 365 is absolutely critical. Backups are the most fundamental way to protect your data. Most organizations have a good handle on backups when it comes to on-premises data, however, when data is migrated to the cloud, backups can get lost in the process.
While there are native mechanisms built into Office 365 that many organizations attempt to use as a means to backup their data. These include File Restores, in-place policies, and retention holds. Files restore is the only one of the three native mechanisms that is supported for data recovery.
Even with File Restores, you can only recover versions of your data up to 30 days old. In addition to this limitation, it does not cover all Office 365 services your business may use.
In lieu of these limitations, using a true enterprise backup solution for your Office 365 environment is absolutely critical to protect Office 365 from data loss. SpinOne provides the backup tools you need to protect your Office 365 environment. With SpinOne you get:
- Automated backups 1-3x daily
- Ability to choose where backups are stored (even in different clouds)
- Ability to choose your own retention policy for your backup data
- Office 365 recover deleted items capabilities
- Efficient incremental backups
- Ability to migrate data between user accounts
- Encrypted backups both in-flight and at-rest
- Centralized administration dashboard
- Advanced reporting on your backup data
Not only does SpinOne allow protecting Office 365 by way of backups, it also includes security for Office 365 to help protect your environment against ransomware. SpinOne’s Ransomware Protection module stops ransomware and automatically restores any Office 365 files that were encrypted.
Concluding Thoughts
Office 365 provides your business with many great features and capabilities that can enhance your end user’s ability to collaborate and be productive. However, with data residing in the cloud, it must be protected. There are many best practices to follow to protect Office 365 from data loss.
By following recommended best practices, it helps to reduce the possibility of data loss. Along with these best practices to protect your Office 365 environment, it is extremely important to backup your data in Office 365. SpinOne provides the ability to backup and secure your Office 365 environment, all in a single solution.
With automated backups and cybersecurity features like ransomware protection contained in SpinOne, you can have confidence in the tools you have available to protect Office 365 from data loss.
Find a Home-Based Business to Start-Up >>> Hundreds of Business Listings.