Abstract:
The article examines the problems of ensuring data security during migration to cloud environments in organizations with increased privacy requirements, such as the public sector and financial institutions. Based on the analysis of theoretical risk management models and practical cases from the experience of certified business analyst, the methodology for integrating cybersecurity requirements into the digital transformation process is considered. The goal of the work is to identify and systematize approaches that minimize risks at all stages of migration, from collecting requirements to implementation and support. The study demonstrated that the use of structured business analysis for mapping security controls, such as SOC, and adapting ITIL standards is a prerequisite for a successful and secure transformation. The results of the study can be applied by IT department managers, cybersecurity specialists, and business analysts to develop strategies for data security during cloud migration.
The transition to cloud technologies is a global trend that allows organizations to increase flexibility, scalability, and cost efficiency. However, for sectors that operate with mission-critical and confidential data—such as government, finance, and healthcare—the migration process entails significant risks. According to a 2023 (ISC)² report, 78% of organizations expressed concerns about cloud security, highlighting the relevance of this issue [1]. Insufficient analysis of security requirements at the early stages of a digital transformation project leads to vulnerabilities, data breaches, and violations of regulatory requirements, such as HIPAA or financial reporting standards.
The purpose of this article is to analyze and substantiate approaches to ensuring data security during cloud migration, based on a synthesis of theoretical concepts and practical experience. The empirical basis includes case studies from the practice of Natalia Stashevskaya, a Certified Business Analysis Professional (CBAP), implemented in Fortune 500 companies and government institutions.
Risk Management in Cloud Migration
The foundation of secure cloud migration is proactive risk management, which begins long before technical implementation. Modern approaches to cybersecurity, such as the NIST Cybersecurity Framework, offer a structured methodology consisting of five functions: Identify, Protect, Detect, Respond, and Recover [2]. In the context of cloud migration, the Identify function takes on particular importance. It involves an in-depth analysis of business processes, data assets, and regulatory obligations to uncover potential threats.
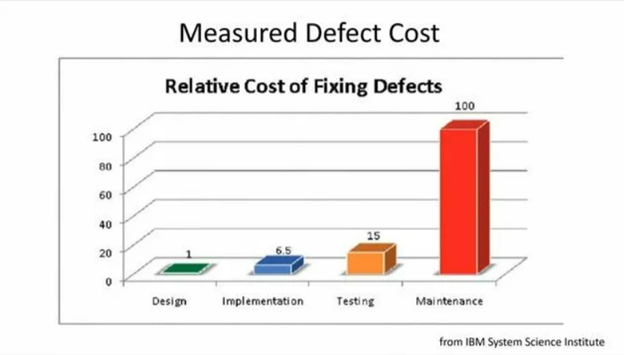
At this stage, business analysis plays a central role. A specialist in this field acts as a bridge between business stakeholders and technical teams, translating business objectives into specific non-functional security requirements. According to research, integrating security analysis in the early stages of the system development life cycle (SDLC) can reduce the cost of fixing vulnerabilities by up to 100 times compared to addressing them during the operational phase [3]. Thus, the theoretical framework for secure migration is built on the principles of early risk identification and the formalization of security requirements using recognized frameworks.
Business Analysis as a Tool for Ensuring Security
In practice, theoretical models are implemented through specific business analysis methods and tools. The process begins with gathering and analyzing requirements, using techniques such as stakeholder interviews, workshops, and documentation review. At this stage, data categories, levels of confidentiality, and sovereignty requirements—that is, the physical location of data within a specific jurisdiction—are defined.
An example can be seen in a digital transformation project at the financial corporation State Street. As part of the project, a comprehensive system for evaluating SaaS solutions was created, which included mapping SOC (Service Organization Control) security controls to ensure secure operations. This not only enabled the technical migration but also ensured compliance with strict financial regulatory requirements.
Another important aspect is change management and compliance with ITSM standards such as ITIL. At the international IT company SoftServe, optimizing cybersecurity compliance workflows and aligning engineering efforts with ITIL standards reduced security risks by 15%. Analyzing user needs and optimizing the service request process through automated forms helped accelerate service delivery and increase end-user satisfaction.
The effectiveness of these approaches is confirmed by projects across various sectors:
- Public sector. In a project for the digitalization of Ukraine’s judicial system, an electronic case management system was introduced. The work included creating a framework for analyzing judicial statistics, which not only enabled data-driven decision-making but also helped identify and mitigate potential security risks. This experience demonstrates how, under resource constraints and high bureaucratic load, structured analysis of business processes and data becomes the foundation for secure modernization of government functions.
- IT consulting and business continuity. A notable case comes from SoftServe, where, under force majeure conditions caused by the outbreak of war, there was an urgent need to transfer client data from Europe and the U.S. Thanks to a pre-developed cloud migration strategy and well-defined security protocols, the team successfully evacuated complete datasets from the country without losses. This example illustrates the highest level of risk management maturity—ensuring business continuity under extreme conditions.
- In managing cloud migration strategies for healthcare IT solutions, particularly when integrating AWS and Azure platforms, the main task was ensuring HIPAA compliance. Developing solutions for integrating Electronic Health Records (EHR) required close coordination between clinical staff, IT teams, and third-party vendors to guarantee seamless and secure system interoperability.
The analysis shows that secure data migration to the cloud in critical sectors is not merely a technical task. The success of transformation is determined by the quality of preliminary analytical work. Integrating business analysis methodologies at all stages of the project—from strategy formulation to implementation—makes it possible to identify and formalize security requirements, adapt industry standards, and ensure regulatory compliance.
The experience reviewed in this article demonstrates that a systematic approach, which includes mapping security controls, adapting ITIL and NIST frameworks, and developing business continuity protocols, enables effective risk management even under the most challenging conditions. Recommendations for organizations planning cloud migration include the mandatory involvement of certified business analysts with cybersecurity expertise at the early stages of the project, as well as conducting a comprehensive audit of data and business processes to build an integrated threat model. This approach ensures not only technological modernization but also creates a resilient and secure digital environment.
Nataliia Stashevska: Expert in business analysis and digital transformation
References:
- (ISC)² 2023 Cloud Security Report. (ISC)², Inc., 2023. URL: https://www.isc2.org/research/cloud-security-report.
- Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1. National Institute of Standards and Technology (NIST). 2018. URL: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf.
- Ayfer R., Impagliazzo J., Laxer C. ITiCSE’10 – Proceedings of the 2010 ACM SIGCSE Annual Conference on Innovation and Technology in Computer Science Education: Foreword.
- Subashini S. A survey on security issues in service delivery models of cloud computing. Journal of Network and Computer Applications, 2011.
- Jelonek D. Big Data Analytics in the Management of Business. MATEC Web of Conferences 125:04021, 2017.
- Ross, J. W., Beath, C. M., & Quaadgras, A. How to develop a great digital strategy. MIT Sloan Management Review, 58(2):7–9, 2017.
Find a Home-Based Business to Start-Up >>> Hundreds of Business Listings.